Learn more details about the technology that uses AI to change people’s faces in videos and manipulate audios
Have you ever thought about seeing your face in a random video? Or hear your voice saying things you would never say? Well, this is possible with a technology called deepfake, which allows this manipulation, especially in videos, in a compelling way. See below for more details on what a deepfake is and why you need to be concerned about this technique.
What is deepfake, and why should you be concerned (Vitor Pádua / Tecnoblog)
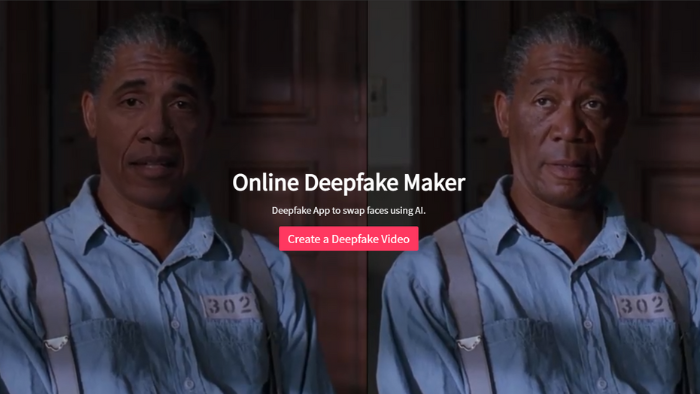
Deepfake uses Artificial Intelligence to change people’s faces in videos and synchronize lip movements, expressions, and other details, in some cases with impressive and compelling results.
This wave of swapping people’s faces in videos is not new. But in December 2017, a Reddit user called deepfakes took it a step further. Using open source Artificial Intelligence and Machine Learning tools such as Keras and TensorFlow (the latter from Google), he created an algorithm to train a Neural Network to map one person’s face onto another’s body, frame by frame.
Instead of relying on manual editing as in the past, the user, through the tool (which was named Deepfake), only needs a source to recognize the model of the “victim’s” face and map the structure of the target head and make the overlap. The software can adjust the movement of the original video to the new beginning, including facial expressions and lip movements.
In the beginning, Deepfake required advanced knowledge on the user’s part. Still, when others created applications and systems capable of automating the entire process, the tool was massively used for evil: dozens of adult videos edited with the software soon began to appear, with the face of actresses and artists.
Deepfake’s “joke” wasn’t limited to adult videos; however: there are several creations that put celebrity faces in movies they weren’t present in. However, the possibilities for using the software are numerous and harmful. Even Mark Zuckerberg was the target of a fake video.
Some examples of easily accessible deepfake tools are the Reface application, the DeepSwap, and DeepFakes Web sites, and the FaceApp and DeepFaceLab programs.
It is important to note that deepfake is different from shallow fake. The premise is the same, but the difference is in the quality. In superficial pretender, the rate of manipulation is lower, making identification easier.
The types of deep fakes
As much as the focus of deepfake is the exchange of faces in videos, anyone who thinks that the practice is restricted to that is wrong. The technique is also used for audio manipulation, where recordings can be created that simulates a particular person’s voice, a type of deepfake that can be easily shared in messengers such as WhatsApp.
In addition, we can already come across textual deepfakes, with typewriters generated by artificial intelligence; deepfakes on social networks, for the creation of fake profiles on the internet; and real-time deepfakes, in which it is possible to change the face in live broadcasts, a technique allowed by the DeepFaceLive software, for example.
Potential risks of deepfakes
Although the main target of the community around the tool is public people, nothing prevents someone malicious from taking a video of an ordinary person and putting it in an embarrassing situation.
Don’t just think about edited porn revenge videos: it’s possible, for example, to forge a moment of relaxation among friends to create an alibi, a statement to convince others that you defend a particular point of view or even a crime situation, way to incriminate him. It all depends on the editor’s creativity, and how many of his videos are readily available on the internet.
As the average quality of the videos is not very high, given the hardware requirements (at least a GeForce GTX 1050 is needed for acceptable results), such creations are pretty convincing to an unsuspecting person, who will think it is an actual video, even if they have a flaw.
Deepfake and elections
The technique is also used in politics. In the 2022 Elections, the first deepfake was already identified with the presenter of Jornal Nacional Renata Vasconcellos. The video features a well-done edit and uses the journalist’s voice to show data from a false poll of intent to vote.
As mentioned above, this content reaches people who cannot immediately identify these montages, increasing the sharing of fake news and misinformation.

Tips for spotting a deepfake
When receiving a questionable video, stop and watch it several times, at all speeds, to make it easier to identify flaws.
Another critical step is to pay attention to the person’s face in the video. Check the skin, eyes, eyebrows, and mouth, for example. These observations make it possible to identify some flaws, be it a slower blink or very smooth or wrinkled skin.
Finally, search for information about the content received (be it video, audio, or text); you may find some news about the subject on the internet. Also, try to find another version of the post so you can compare speech and gestures.
In short, maximum attention to every detail.
What attitudes to take?
So that your content is not used in a deepfake, the most sensible thing to do is to avoid sharing personal videos with people you don’t know or not hosting them on social networks publicly to make the editor’s job more difficult.
In general, society is still adjusting to deepfake because it is a new technology and, if misused, extremely harmful. It is expected that new legal mechanisms will be approved to combat the practice and protect people. Therefore, if you have been a victim, collect all the necessary information and seek a lawyer or the Public Defender’s Office as soon as possible.
In the case of videos and audio received, avoid sharing without first following the tips to identify a deepfake. This attitude is critical to prevent the spread of false information and inappropriate content.
Is it illegal to create deepfake?
Artificial intelligence and deep learning technologies are not a problem as they can be used to create harmless videos. However, the word deepfake is usually associated with dire situations, that is, that put people, social groups, and even democracy at risk.